Dynamic Access Control in Windows Server 2012 and its benefits
The new age security measures on Windows Server 2012 allow administrators to control the way the data is accessed from the file servers. This has improved data classification which enables controlling access to files and auditing them at the same time. Access controls can be applied to critical files which prevents their access by unauthorized users. File security policies are enforced at the domain level, which are then replicated across all file servers. Apart from this, the improved auditing procedures capture any unapproved attempts at accessing protected data, dutifully reflecting these in reports that are accessible by administrators.DAC handles authentication and authorization over and above the Groups Hierarchy common in Active Directory. This is done through
- Classification of Data
- Implementation of Expression Based Access Conditions
- Implementation of Expression Based Auditing
- Encrypting Data
- Claims – from Users and Devices
- Expressions based Access Control Lists
- File Classification Infrastructure
- Auditing and Central Access Policies
- Resolving Access Denied scenarios
1) Classification of Data – Organizing and Tagging Data
The File Classification Infrastructure (FCI) has been strengthened further by making it “claims aware”. With this step, the file’s own properties can be used as properties based on which it is classified. This helps in judging how well the user’s claims fit into the way claims are laid and are allowed on the resources (files). Conditional Access Control Entries are made use of for this purpose. The classification can be carried out manually by system administrators through the Windows Explorer. The use of FCI has also enabled –- Administrators to manually classify the files through the Explorer
- The use of security properties for making decisions under the ambit of the authorization expressions
- Automatic and continuous classification of the files; soon after their creation or after they are modified as well as the way the resource properties are assigned to the files
- Control of the way classification is inherited by the child objects from their parent folder
- Manual tagging of the folder and its contents by the administrator and the file owners
2) Implementation of Expression Based Access Conditions
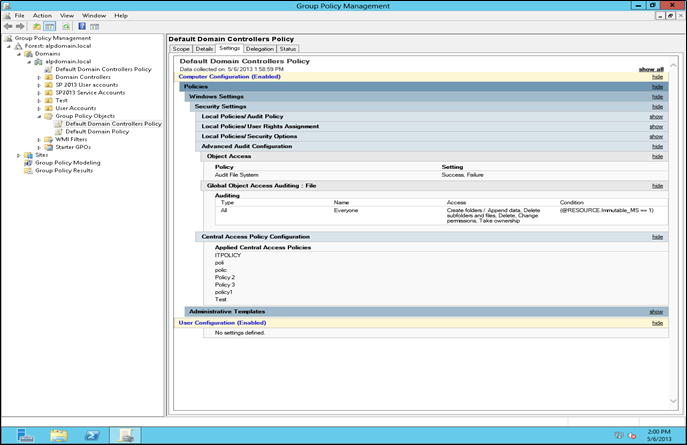
A new feature called the Central Access Policies (CAP) allows you to control how the classified files are accessed. This feature allows users access to files only after they satisfy specific requirements which are set by the administrators and owners. This means you can control the way the classified files are accessed either through networked computers or other smart access devices, for example cards. This also means that intended users are quickly provided remediation whenever they face access-denied situations. This reduces the time and effort administrators have to spend on troubleshooting and providing access-denied assistance.CAPs buttress the local access policy and the Discretionary Access Control Lists (DACLs) that may have been applied to files. This means, if there is a “deny” in the CAP but not in the ACL or the local access policy, the “deny” still takes precedence. To be accessible, the file must have been granted access at all levels. CAPs are built upon Access Control Entries (ACEs) that govern access to the data and the defined condition that determine which files fall under its scope.Here is a sample CAP configuration (figure 1).With Central Access Policy (CAP) in place the file classification effort can be combined with Expression Based Access Control. Thus in any organization with structured and layered distribution of business critical data, applied access conditions will only permit those with division level and project level authorizations to access the data. The applied group policies control such access to the file servers.
- Checking the ACLs
- Checking the Central Access Policies
- Checking the NTFS based file ACL entries
3) Implementation of Expression Based Auditing
With better auditing policies in Windows Server 2012, you can carry out a forensic analysis of the number of attempts at accessing a protected file in the file server. The “grant’s” and “deny’s” you set under the Central Audit Policies help you determine who attempted to access a secured file and how many of these attempts were successful. The claims based authorization process allows smoother and better auditing through Global Object Access Auditing and Group Policies. This also allows for targeted monitoring (monitoring specific type of data) as well as compliance of files on the file server.An advantage with such method of auditing is that the number of events to be monitored can be limited to only those necessary. And when tagged data is monitored with such auditing policies it allows for contextual reporting.If there are adequate number of Windows Server 2012 and Windows Server 2008 domain controllers spread throughout your network, monitoring and authorizing requests to the Windows Server 2012 file servers, you can configure and enforce claims based auditing. This also means that the Windows Server 2012 has better Kerberos armoring, as the claims ride within an envelope of Kerberos Ticket and compound authentication. The Kerberos Key Distribution Center (KDC) has been enhanced to enable such authorizing and auditing.4) Encrypting Data
The encryption applied to secured files is based on data classification. Files containing sensitive data can be encrypted automatically through Rights Management Service (RMS). The continuous file management tasks running in the background on servers can detect files marked sensitive and automatically start applying RMS protection. This means, even if the file is inadvertently moved or copied out of its circle of use, it will still be inaccessible to unintended users as they will have to get the authentication from the RMS server, which will then hand the decryption key. Without it, the file is locked and inaccessible.Adoption of Dynamic Access Control and the subsequent implementation of Central Access Policies require sophisticated tools that help manage and control all aspects of DAC / CAP – especially tracking, reporting and applying central policies that provide advanced and more sophisticated control on NTFS permissions on folders and files.Vyapin’s solutions to the challenge of auditing and managing Windows File Servers
Vyapin offers two proprietary solutions to audit and manage DAC / NTFS permissions on Windows servers. They are:Here is a brief on both these products along with some representation of their auditing and permissions management capabilities.1) NTFS Security Auditor
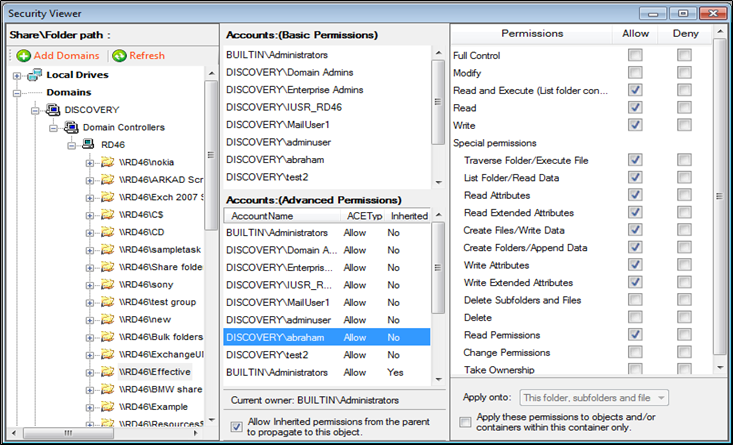
This is a comprehensive NTFS permissions auditing solution that covers all aspects of Windows File Server audit like the permissions of users and groups on files, folders and shares. It provides useful insights on how the security of your Windows network is organized by providing you with a detailed report on the ACLs of shares, folders and files.Here is a list of some of the benefits it offers.- Determine what permissions have been configured for each of the Central Access Rules
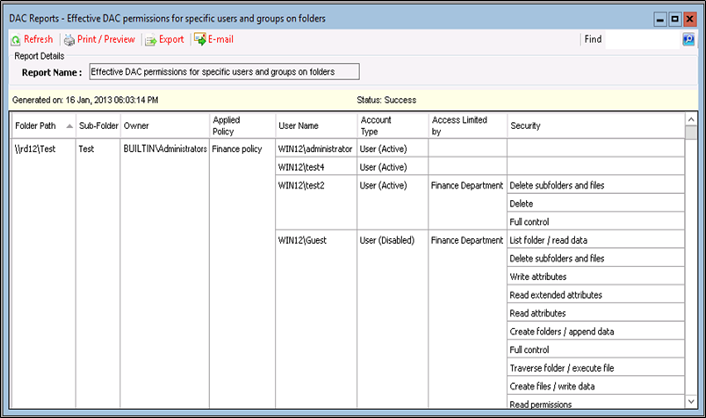
- Determine the effective permissions of users on shared folders based on DAC / CAP
- Determine which shared folders fall within or lie outside the purview of the Central Access Policy
- View the NTFS permission of various servers and workstations spread across domains
- Find out users with inadvertently assigned permissions due to their group memberships
- Determine effective permissions arising out of explicit permissions, inherited permissions and those obtained by memberships of nested groups
- View a summary of all shares
- Use customized search to find out users with a unique set of permissions
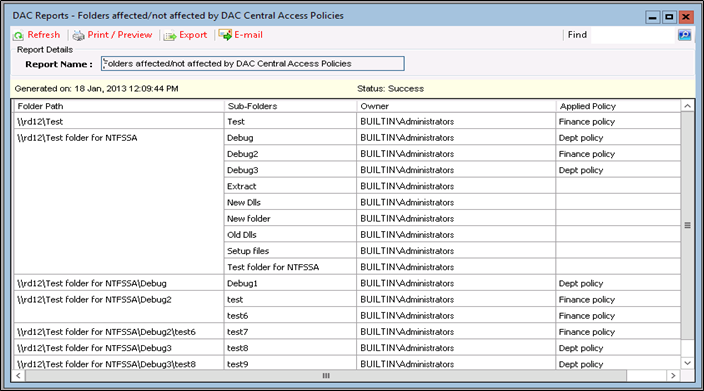
1.1) Here is a DAC Report showing details of the folders that are either affected or not affected by the DAC Central Access Policies.
2) NTFS Security Manager
This is an NTFS permissions management solution that helps you improve the security of shares, folders and files on Windows servers and workstations. It helps you grant, revoke, modify and copy NTFS permissions according to the built-in rules for assigning permissions.Here is a list of some of the benefit it offers.- Grant, revoke modify and copy NTFS permissions across servers and workstations in multiple domains
- Clean up unwanted permissions
- Restore administrative permissions and broken inheritance
- Set multiple permissions in bulk for accounts and folders
- Search for atomic and molecular level permissions on files and folders
- Use the Change History to track all changes made in permissions using the Security Manager
About Vyapin
Vyapin develops Management, Migration, Reporting, Auditing, Configuration, Administration & Reporting solutions for Microsoft products. Our solutions help reduce man-hours spent on time-consuming and resource-heavy activities that burden IT administrators and managers.Our products are designed and built to:- Deliver substantial savings in the time and cost incurred on various projects.
- Improve IT infrastructure and systems utilization in companies big or small.
- Provide better value for money and a substantial return on investment.

2A, "K. G. Sunshine", No. 48, 12th Avenue
Ashok Nagar, Chennai - 600083, India
Disclaimer
Vyapin makes no representations or warranties with respect to the accuracy or completeness of the entire content of this document. Vyapin reserves the right to make changes to the specifications and product descriptions at any time without notice. Vyapin does not make any commitment to update the information contained in this document.Vyapin assumes no liability whatsoever and disclaims any express, implied or statutory warranty relating to its products including, but not limited to, the implied warranty of merchantability, fitness for a particular purpose, or non-infringement. Under no circumstances shall Vyapin be liable for any direct, indirect, consequential, punitive, special or incidental damages (including, without limitation, damages for loss of profits, business interruption or loss of information) arising out of the use or inability to use this document, even if Vyapin has been advised of the possibility of such damages.The information in this document is provided in connection with Vyapin’s products. This document contains proprietary information protected by copyright. No part of this document may be reproduced or transmitted in any form or by any means, electronic or mechanical, including photocopying and recording for any purpose without the written permission of Vyapin Software Systems (P) Limited.
Copyright © Vyapin Software Systems (P) Ltd. All rights reserved